A German IoT manufacturer engaged Oxeltech to achieve RED Cybersecurity compliance for a battery-powered STM32F4-based device using an external WiFi module. Though functional and deployed globally, the device lacked secure communication, authenticated access, and safe OTA updates—requirements under the RED Delegated Act 2022/30 effective from August 2025.
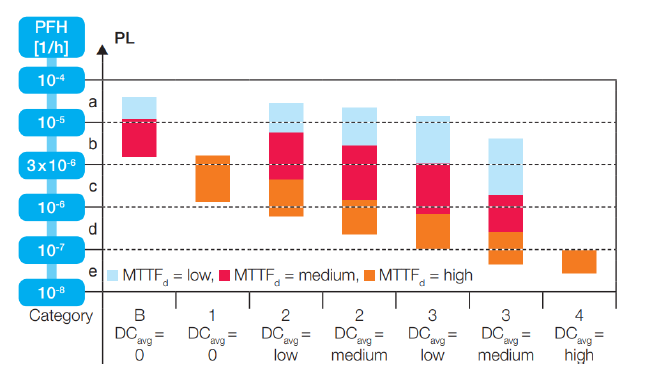
Oxeltech conducted a gap analysis using ETSI EN 303 645 and identified key risks: default credentials, insecure OTA, exposed debug interfaces, plain HTTP communication, and no vulnerability disclosure process. The product also lacked a documented security lifecycle policy.
Oxeltech implemented mbedTLS, STM32 SBSFU bootloader, and a secure OTA process. They provisioned unique keys per device, disabled unnecessary services, and designed a secure pairing protocol. Documentation included a RED-aligned risk assessment and a technical file.
The outcome: full RED Cyber DA compliance without hardware redesign, preserved low-power operation, and CE readiness before the deadline. The client’s embedded team was also trained for future compliance.
Oxeltech also supports ESP32, nRF52, and other MCU-based devices to meet RED cybersecurity requirements.
To read this in more detail, click here.
The task involved identifying components that were certified by both UL USA and UL Canada, ensuring compliance with safety standards for the BMS project.
Application:
Tools Used:

The primary objective of this project was to obtain UL certification for safety standards pertaining to the BMS through comprehensive analysis and safety grading assessment of the entire system.
Application: